Explore Microsoft Security Services
We believe that a strong security operations center is the foundation of any effective cybersecurity strategy

Modern Security Operations Center
Strengthen Your Security Posture With AI
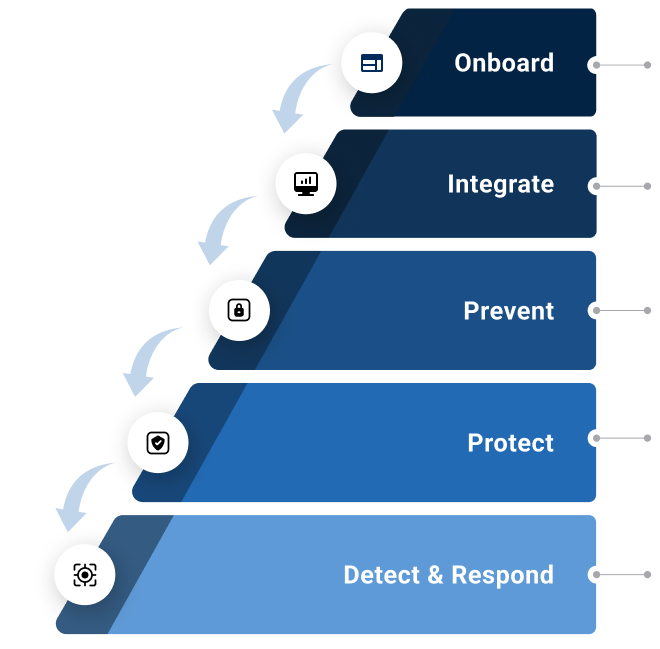
With our onboarding process, we proactively monitor, detect, and respond to potential security events, ensuring your digital assets are safeguarded with the highest level of vigilance and expertise.
Integrate data connectors to establish a unified dashboard, providing a comprehensive view of security events across all systems and platforms for streamlined monitoring and rapid response
Prevent strategies proactively fortify your systems against potential threats, utilizing advanced threat intelligence and proactive measures to thwart attacks before they occur.
Our Service Offerings
Unparalleled Security Solutions for Tomorrow’s Challenges
Advisory And Consulting
Offer expert guidance for implementing and maintaining strong security posture, including workshops, tailored security architecture design, and proof of concept development
Identity & Endpoint Protection
Data Protection
Security Risk Assessment
Advanced Training
Modern Security Operations Center
Let's Answer Your Why & How?


What are the benefits of SOC?
Partnering with our SOC provides numerous benefits
End-to-end technology solutions for your business success
- Experienced Professionals
- Top-notch Services
- Industry Expertise
- Client Dedication
- Customizable Solutions
- Tailored Strategies
- Business Alignment
- Collaborative Approach
- High-Quality Services
- Proven Solutions
- Client Satisfaction
- Cyber Threat Protection
Did You Know?
Frequently Asked Questions
Common questions about our security services
SOC stands for Security Operations Center. It is a centralized unit that is responsible for monitoring and analyzing an organization’s security posture.
SOC is important because it helps organizations identify and respond to security threats in a timely and effective manner, which can prevent data breaches and other security incidents.
SOC can help organizations comply with industry regulations and standards by providing a framework for identifying and responding to security threats.
Best practices for SOC implementation include having a clear understanding of your organization’s security risks, establishing clear processes and procedures, investing in the right technology, and regularly reviewing and updating your security strategy
Don’t wait for a security breach
Partner with our experts and learn how to stay protected!